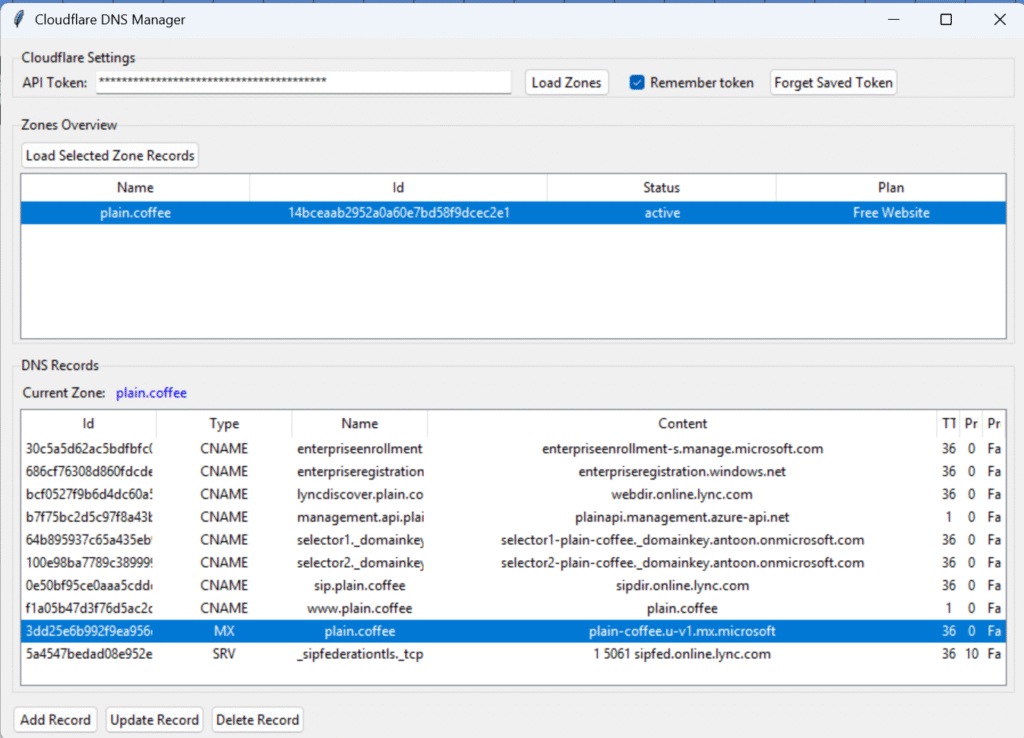
If you manage multiple domains in Cloudflare, small DNS changes can add up to a lot of clicks. The built‑in UI is great for one zone, but less convenient when you jump between many zones or handle frequent cut‑overs.
Cloudflare DNS Manager is a lightweight Windows desktop app that sits in between. It uses Cloudflare’s API to list your zones and edit DNS records in a single, fast, searchable view. You authenticate with a Cloudflare API token, not the global API key, so you can limit access to exactly what is needed.
Who it is for
- Every organization that want specific people to manage specific domains on Cloudflare without access to the admin portal
- DevOps, support and on-call engineers handling urgent cut‑overs
- Teams that prefer a simple UI, quick UI, over the advanced but bloated Cloudflare web interface
What you can do
- Load all zones tied to your token, then browse records per zone
- Add, update, or delete DNS records with a couple of clicks
- Filter and sort by name, type, TTL, priority and proxied status
- Work with a least‑privilege API token that you can revoke at any time
How it works under the hood
- The app connects to Cloudflare’s REST API using your token
- It fetches your zones (that you have permission to), then lists DNS records for the selected zone
- Changes you make are sent as API calls; responses are shown and propagated immediately
- Your token can be remembered locally on your machine if you opt in
Create a Cloudflare API token
Sometimes you want to give a colleague or partner access to one domain, or even all.
You can do this without inviting them into your Cloudflare account by issuing a restricted token.
Go to My Profile > API Tokens > Create Token.
Choose Custom Token (or start from “Edit zone DNS” and adjust).
Permissions:
Zone.DNS: Edit
Zone.Zone: Read
Resources:
Include > Specific zone (recommended) or All Zones
Optional:
Set an expiration date so access ends automatically
Add an IP filter to restrict where the token can be used from
Create the token and share only this token with the person who needs access.
They can paste the token into API CDNS Manager and will see only that zone.

Installation
- Windows desktop app (portable)
- No additional dependencies required
- For now, only Windows
Download: https://trustmyl.ink/cdns-download